Introduction
Using the KMS (Key Management Service) in AWS you can encrypt your data at rest on your RDS instance. In today's IT world with an ever-growing need to better secure your data in the cloud, AWS provides the tools needed to accomplish this need. Encryption helps to protect your company data, any client data, or both which may be stored on your RDS instance(s). Without access to the private key used by KMS encryption, anyone who should not have access to your data does not have access to view the contents of your data.
Limitations
- You can not encrypt an existing RDS instance in AWS. You will be required to create a new RDS instance to encrypt your data.
- Encrypted DB instances can’t be modified to disable encryption after encryption has been enabled.
- Two RDS instances can not have the same name. You will need to modify an existing RDS instance name if you want to reuse the same name for your new RDS instance.
Steps for Implementing
- You must log into your AWS account and navigate to the RDS service (be sure to select the appropriate region your resource is located in)
- On the left sidebar, you will click on “Databases” which will provide you with the list of your RDS instance in the current region of your account.
- Select your RDS instance and on the right side of the page click on the dropdown “Actions” and choose “Take a snapshot”. (While the snapshot is being performed you may experience performance degradation and or total loss of traffic to the RDS instance until the status of the RDS instance returns to an “Available” state).
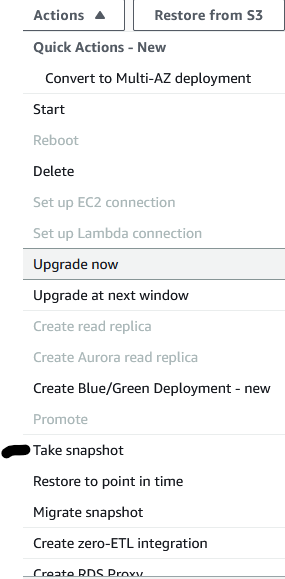
- Provide the snapshot name of your choice and then click the orange button “Take snapshot”.
- To view your snapshot status, on the left sidebar you can click on “Snapshots”.
- You will then need to click on “Manual” in the top middle of your screen.
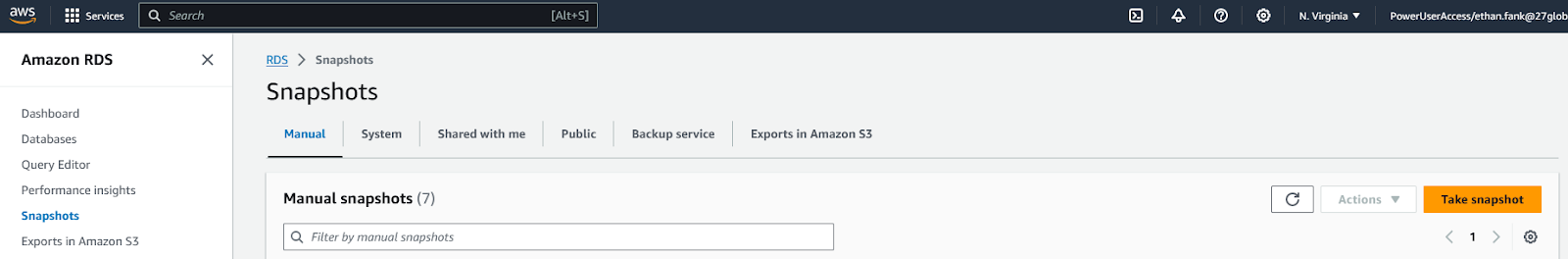
- Next, you will select the snapshot you created and click on “Actions”.
- Select “Copy snapshot” and fill in the following fields
a. Destination Region - choose the region you want the snapshot created in
b. New DB Snapshot identifier - Name you will give this encrypted snapshot
c. Check the “Enable Encryption” box
d. AWS KMS key - Select either the AWS-managed KMS key for RDS or you can select a customer-managed key in KMS if your company manages their own keys.
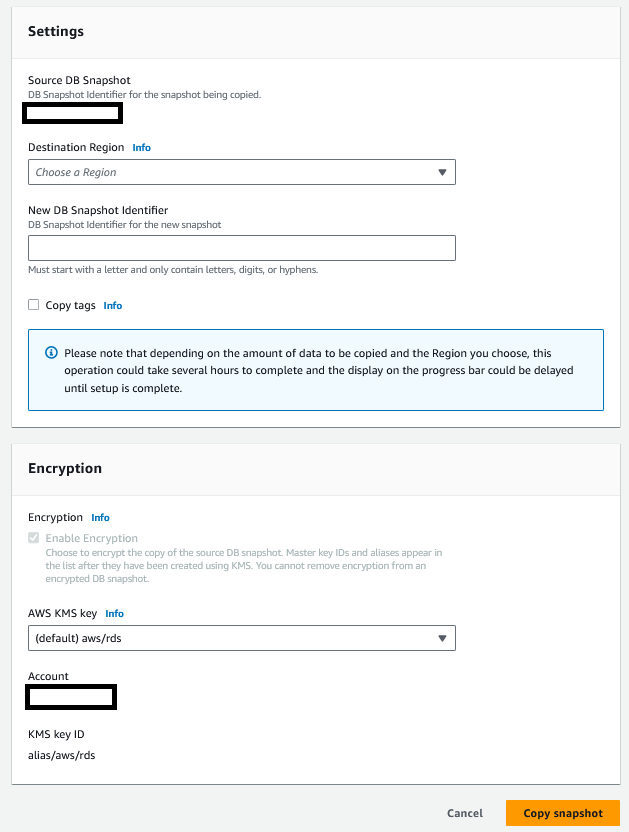
- Click the orange button “Copy snapshot” at the bottom right of the page.
- Next, you will need to wait for the encrypted snapshot to complete which will be in the same “Manual” view from step 6.
- Once the new encrypted snapshot is completed you will then create a new RDS instance from the encrypted snapshot.
- Select your encrypted snapshot and click “Actions”
- Click “Restore snapshot”
- Choose the requirements your encrypted RDS instance will need (if you are unsure of the option you can look at the existing RDS instance to see its configuration)
- Click the orange button “Restore DB instance”
- You may now remove your old unencrypted RDS instance after testing if it is no longer needed.
- Your RDS data is now encrypted at rest for your RDS instance. Something to be aware of is that RDS instances can not be stopped indefinitely. If you stop your current un-encrypted RDS instance it will only stay stopped for 7 days after which AWS automatically starts the stopped RDS instance.
Conclusion
This process can be performed when you initially create your RDS instance or you can create a new RDS instance from your existing RDS instances snapshot to encrypt your existing database. When encrypting an unencrypted RDS instance it is useful to know that if performed outside of your companies or AWS scheduled maintenance window for your RDS instance, some downtime will occur. While the snapshot finishes creating and your RDS instance is in a ‘Backup’ state you may experience a degradation of service or a complete connection drop while the RDS instance is in this state.




